他、她、㐅也、男也……
在 2025.9.9 发布的新版国际统一字符编码 Unicode 17.0 里,新增了 4803 个字符,出现了汉字的「㐅也」和「男也」,这下人称代词齐了~
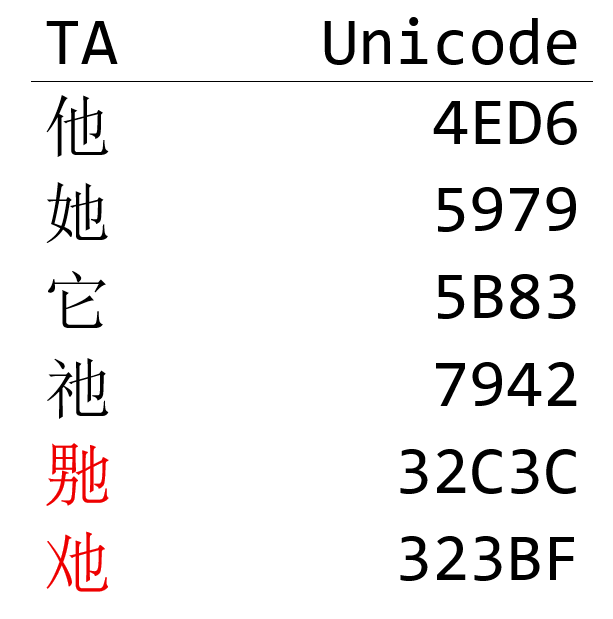
追踪这两个新字被提交到 Unicode 的过程。这一批新字,在 2024.6.26 被正式提交(Proposal on new CJK Unified Ideographs Extension for IRG WS2021),而早在 2021 年,就已经出现在表意文字研究小组(Ideographic Research Group,IRG)的讨论区 WS2021 里。从上面的 Proposal 可以直接点击进入每个字的讨论页面。
从讨论过程和提交的字源证据中,可以看出,提交「㐅也」和「男也」的,大概不是同一批学者。「男也」是对新文化运动中涌现出的文字的拾遗补缺;而「㐅也」则是专门为了非二元性别而造出来的。
男也:
众所周知,(女也,她)是刘半农大力推出来的。早在 1918 年,周作人就在《新青年》上聊过,刘半农想要造一个「她」来翻译 she。1920 年,刘半农发表了《“她”字问题》,和脍炙人口的《教我如何不想她》,代表着女性代词「她」被广泛接受。
这场关于女性代词的讨论,在当时影响很大。不难想象,有了「女也」之后,就有人想要有「男也」,而且,是打着「专门提升女性地位,是对男性不公平」的旗号。提交的最早的关于「男也」的字源证据,是 1922.9.14 《现代妇女》的稿件。文章里主要谈的是:有了专门的女校之后,很多男人觉得不公平,认为被女性抢占了教育资源。然后顺便提到:
某报上有位先生,做了篇文章,中间用了许多『男也』字,累铸字房的工人忙得汗如雨下。——据说是替『她』字复仇的。

后来也有一些看起来没那么男权味道的讨论,在区分「女也、男也」的同时,还有「子也、牛也」……甚至出现在 1935 年的《初中精讀國文範程》(潘尊行編著)。但后来为什么只有「女他」成为了常用字,就不得而知了。
㐅也:
「㐅也」的提交者是英国汉学家 Andrew C. West(魏安)(1960-2025),今年 7 月刚刚去世。最早关于「㐅也」的字源证据,是 2019.2 香港的《性别空间 2018 年度报告》。

「㐅也」并不是从久远的文献中翻出来的,而是根据现代需要造出来的全新的字,这在 Unicode 的编码中很少见。在提交页面上,也有过一些讨论,譬如这个字是应用于跨性别群体、还是更广泛的非二元性别群体;以及「㐅」会不会让人感觉到「非人」的贬义。但都没有太大的阻碍。反对者王谢杨在 2011 年刚出草案时,就在知乎上吐槽过这是否算政治正确需要再缓一缓,但正式页面的讨论直到 2023 年才出现。
那么,如何输入这些新字呢?从字形被加入 Unicode 编码,到这个编码出现在各种常用字体字库,乃至出现在常用的中文输入法里,用纯文本发出去直接被对方看到,中间还有很长的过程。
想要尝新的话,「字雲 Jigmo」和「全宋體」都已经做好了 Unicode 17 新增的这些汉字(后者似乎有一些版权问题)。 下载安装字体后,就可以在各种文本或图片编辑器里使用、打印或者截屏输出了。
如何输入 Unicode 字符?在微软 Office 里,可以输入 Unicode 编码(譬如 32c3c)然后在末尾按下(Alt + x);也可以直接复制下面的乱码文字。
「男也」=「」
「㐅也」=「」